The universal Envoy service mesh
for distributed service connectivity
The open-source control plane for service mesh,
delivering security, observability, routing and more
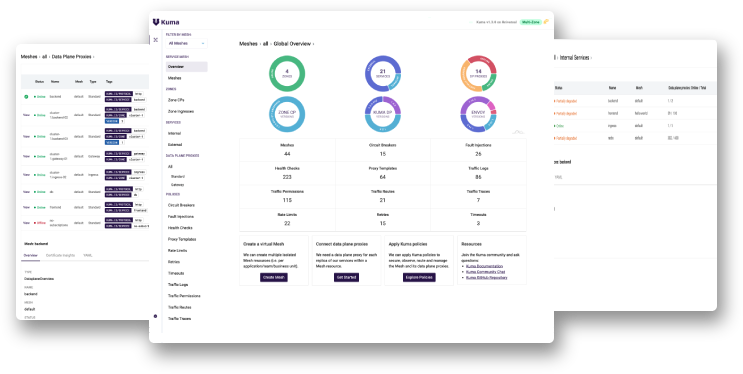
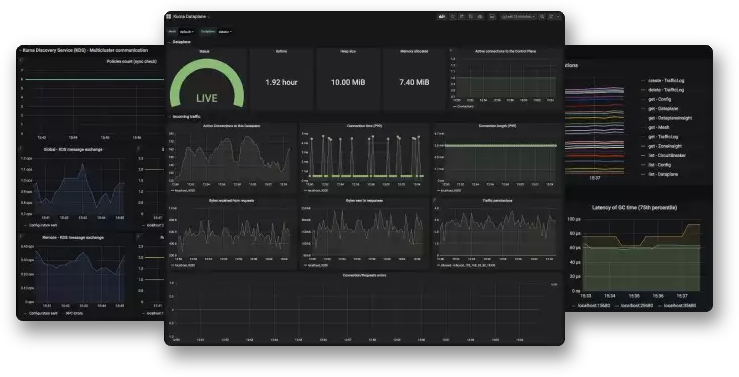
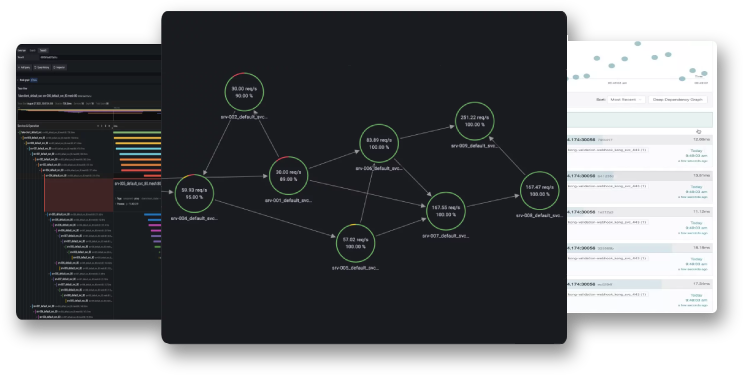
News
Kuma 2.9.0 has been released! — with MeshTLS, service rewrite and more on the Kuma 2.9.0 release blog post.



 Aaron Weikle, CEO of MS3
Aaron Weikle, CEO of MS3We chose Kuma in large part because we needed a solution that would allow our customers to support both Kubernetes and virtual machines, while providing an easier path to migrating between the two.
Kubernetes, VMs & Multi-Mesh
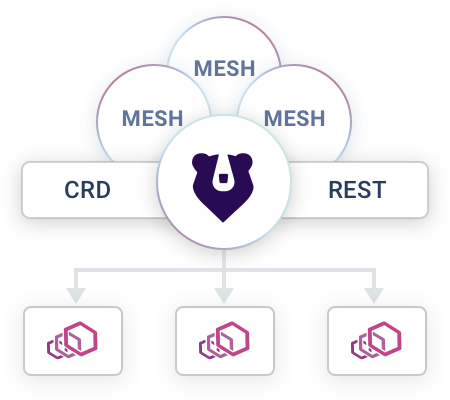
Built on top of Envoy, Kuma is a modern control plane for Microservices & Service Mesh for both K8s and VMs, with support for multiple meshes in one cluster.
Easy To Use & Upgrade

Out of the box L4 + L7 policy architecture to enable zero trust security, observability, discovery, routing and traffic reliability in one click. Easy, yet powerful.
Multi-Cloud & Multi-Cluster
Built for the enterprise, Kuma ships with the most scalable multi-zone connectivity across multiple clouds & clusters on Kubernetes, VMs or hybrid.
Install Kuma via an available distribution:
kumactl install control-plane \
| kubectl apply -f-
Visualize the GUI to see your cluster:
kubectl port-forward svc/kuma-control-plane \
-n kuma-system 5681:5681
Navigate to 127.0.0.1:5681/gui to see the GUI.
Install Kuma via an available distribution:
kumactl install control-plane \
--cni-enabled | oc apply -f -
Visualize the GUI to see your cluster:
oc port-forward svc/kuma-control-plane \
-n kuma-system 5681:5681
Navigate to 127.0.0.1:5681/gui to see the GUI.
Install Kuma via an available distribution:
kuma-cp run
Navigate to 127.0.0.1:5681/gui to see the GUI.
Start in minutes, not in days
Getting up and running with Kuma only requires three easy steps. Natively embedded with Envoy proxy, Kuma Delivers easy to use policies that can secure, observe, connect, route and enhance service connectivity for every application and services, databases included.
- Bundled with Envoy Proxy. No Envoy expertise required.
- 10+ Policies ready to use for all L4 + L7 traffic in the organization.
- Ships with native CRDs and a GUI + REST API and a CLI too.
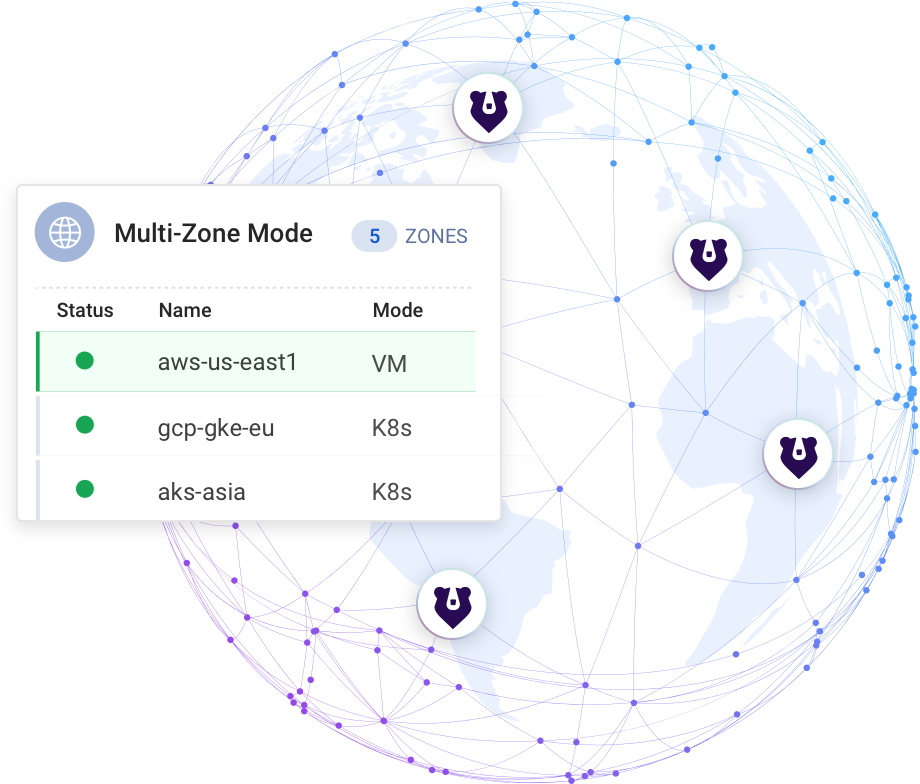
Single and Multi-Zone Connectivity
Build modern service and application connectivity across every platform, cloud and architecture. Kuma supports modern Kubernetes environments and Virtual Machine workloads in the same cluster, with native multi-cloud and multi-cluster connectivity to support the entire organization.
- Multi-zone deployment for multi-cloud and multi-cluster.
- Kubernetes and VMs support, including hybrid.
- Native Ingress, Gateway and multi-mesh support.
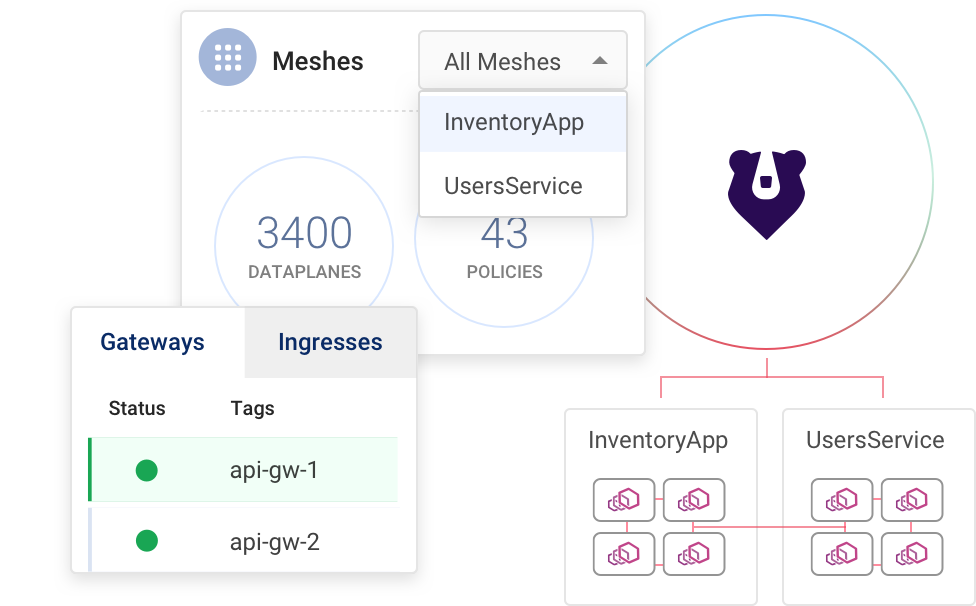
One cluster for the entire organization
Designed for the enterprise architect, Kuma ships with a native multi-mesh support to support multiple teams from one control plane. Combined with native service discovery, global and remote deployments modes, and native integration with APIM solutions, Kuma checks all the boxes.
- Built for the enterprise architect for mission-critical use-cases.
- Multi-Mesh from one control plane to lower Ops complexity.
- Scalable horizontally in standalone or multi-zone mode.
Ready to get started?
Receive a step-by-step onboarding guide delivered directly to your inbox
Thank you!
You're now signed up for the Kuma newsletter.
Whoops!
Something went wrong! Please try again later.
Ready to get started?
Receive a step-by-step onboarding guide delivered directly to your inbox
Thank you!
Whoops!
Something went wrong! Please try again later.
